Top Posts

“Streamlined” is an adjective most people wouldn’t normally associate with debt ...

“Streamlined” is an adjective most people wouldn’t normally associate with debt ...
“Streamlined” is an adjective most people wouldn’t normally associate with debt ...
SentinelOneOne way or another, passwords are always in the news. They’re either being stolen in data breaches, or mocked for being too simple; derided as pointless, or lamented for being technologically backward. No matter what opinion any of us have on passwords, though, one thing is indisputable: we’re going to be using them today, tomorrow and for the forseeable future. Unlike touch or facial recognition technologies, passwords are used everywhere because they’re cheap to implement and simple to use. For end users, they are as low-tech as security tech ever gets. Of course, that ubiquity and simplicity is precisely what makes passwords attractive to thieves. In this post, we take a look at how hackers steal our passwords and what we can do to stop them.
1. Credential Stuffing
Risk Level: High
It is estimated that tens of millions of accounts are tested daily by hackers using credential stuffing.What Is It?
Credential stuffing, also known as list cleaning and breach replay, is a means of testing databases or lists of stolen credentials – i.e., passwords and user names – against multiple accounts to see if there’s a match.How Does It Work?
Sites with poor security are breached on a regular basis, and thieves actively target dumping user credentials from such sites so that they can sell them on the dark net or underground forums. As many users will use the same password across different sites, criminals have a statistically good chance of finding that userjanedoe@somesite.net has used the same password on janedoe@anothersite.com. Tools to automate the testing of a list of stolen credentials across multiple sites allow hackers to quickly breach new accounts even on sites that practice good security and password hygiene.
How Can You Stay Safe?
The key to not becoming a victim of credential stuffing is simple: every password for every site should be unique. Of course, that won’t prevent your password being stolen for one account on a site with poor security, but it does mean that any one compromise of your credentials will not affect you anywhere else on the internet. If you’re gasping at the thought of creating and remembering unique passwords for every site you use, see our Tips section near the end of the post.2. Phishing
Risk Level: High
Over 70% of all cybercrimes begin with a phishing or spear-phishing attack. Hackers love to use phishing techniques to steal user credentials, either for their own use, or more commonly to sell to criminals on the dark net.What Is It?
Phishing is a social engineering trick which attempts to trick users into supplying their credentials to what they believe is a genuine request from a legitimate site or vendor.How Does It Work?
Typically, but not always, phishing occurs through emails that either contain fraudulent links to cloned websites or a malicious attachment. Somewhere along the chain of events that begins with the user taking the bait, the fraudsters will present a fake login form to steal the user’s login name and password. Fraudsters will also use some form of interception between a user and a genuine sign-in page, such as a man-in-the-middle attack to steal credentials.How Can You Stay Safe?
Use 2-factor or multi-factor authentication. Although researchers have developed tricks to overcome these, in the wild cases are yet to be reported. Caution is your number one defense against phishing. Ignore requests to sign in to services from email links, and always go directly to the vendor’s site in your browser. Check emails that contain attachments carefully. The majority of phishing emails contain misspellings or other errors that are not difficult to find if you take a moment to inspect the message carefully.3. Password Spraying
Risk Level: High
It’s been estimated that perhaps 16% of attacks on passwords come from password spraying attacks.What Is It?
Password spraying is a technique that attempts to use a list of commonly used passwords against a user account name, such as123456, password123, 1qaz2wsx, letmein, batman and others.
How Does It Work?
Somewhat like credential stuffing, the basic idea behind password spraying it to take a list of user accounts and test them against a list of passwords. The difference is that with credential stuffing, the passwords are all known passwords for particular users. Password spraying is more blunt. The fraudster has a list of usernames, but no idea of the actual password. Instead, each username is tested against a list of the most commonly used passwords. This may be the top 5, 10 or 100, depending on how much time and resources the attacker has. Most sites will detect repeated password attempts from the same IP, so the attacker needs to use multiple IPs to extend the number of passwords they can try before being detected.How Can You Stay Safe?
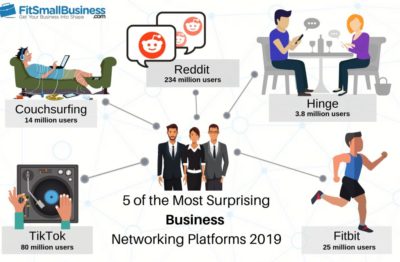
Ensure your password is not in the list of top 100 most commonly used passwords.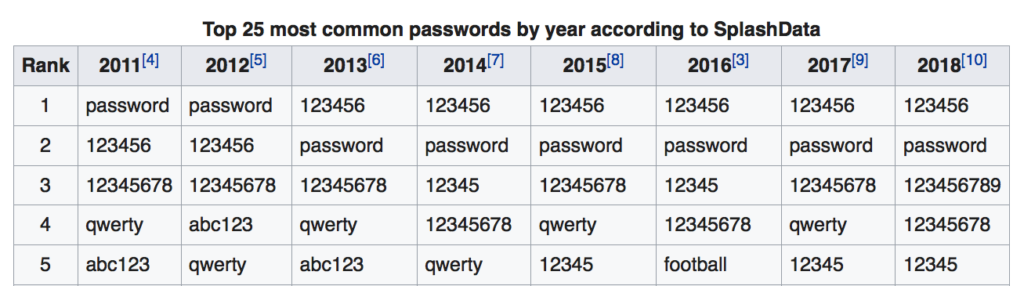
4. Keylogging
Risk Level: Medium
Keylogging is often a technique used in targeted attacks, in which the hacker either knows the victim (spouse, colleague, relative) or is particularly interested in the victim (corporate or nation state espionage).What Is It?
Keyloggers record the strokes you type on the keyboard and can be a particularly effective means of obtaining credentials for things like online bank accounts, crypto wallets and other logins with secure forms.How Does It Work?
Keylogging is more difficult to pull off than Credential Stuffing, Phishing and Password Spraying because it first requires access to, or compromise of, the victim’s machine with keylogging malware. That said, there are lots of publicly available post-exploitation kits that offer attackers off-the-shelf keyloggers, as well as commercial spyware tools supposedly for parental or employee monitoring.How Can You Stay Safe?
You need to be running a good security solution that can detect keylogging infections and activity. This is one of the few kinds of password theft techniques where the strength or uniqueness of your password really makes no difference. What counts is how well your endpoint is secured against infection, and whether your security software can also detect malicious activity if the malware finds a way past its protection features.5. Brute Force
Risk Level: Low
Surprisingly not as prevalent as people tend to think, brute forcing passwords is difficult, time-consuming and expensive for criminals.What Is It?
It’s the kind of thing that security researchers like to write about, or which you might see in TV shows: a hacker runs an algorithm against an encrypted password and in 3…2…1… the algorithm cracks the password and reveals it in plain text.How Does It Work?
There are plenty of tools like “Aircrack-ng”, “John The Ripper”, and “DaveGrohl” that attempt to brute force passwords. There’s generally two kinds of cracking available. The first is some form of “dictionary” attack – so called because the attacker just tries every word in the dictionary as the password. Programs like those mentioned above can run through and test an entire dictionary in a matter of seconds. The other type of technique is used when the hacker has (through means of a data breach) acquired the hash of the plain-text password. Since these can’t be reversed, the aim is to hash as many plain-text passwords as possible and try to find a match. Rainbow tables exist which list the hashes of common passphrases to speed up this process. One of the reasons why password cracking is not as viable a technique as some of the others we’ve mentioned is that encrypted passwords typically use a salt. This is some random data used in the encryption process that ensures no two plain-text passwords will produce the same hash. However, mistakes made by site administrators when using or storing salts and passwords can make it possible for some encrypted passwords to be cracked.How Can You Stay Safe?
The key to staying safe from brute force attacks is to ensure you use passwords of sufficient length. Anything 16 characters or over should be sufficient given current technology, but ideally future-proof yourself by using a passphrase that is as long as the maximum allowed by the service that you’re signing up to. Avoid using any service that doesn’t let you create a password longer than 8 or 10 characters. Worried about how you’d remember a super long password? See the Tips section below.6. Local Discovery
Risk Level: Low
Mostly a technique that would only be used in a targeted attack, either by a known acquaintance, relative, colleague or law enforcement.What Is It?
Local discovery occurs when you write down or use your password somewhere where it can be seen in plain text. The attacker finds the password and uses it, often without your knowledge that the password has been leaked.How Does It Work?
You’ve seen those movies where the cops go through the bad guy’s trash for clues as to what he’s been up to? Yep, dumpster diving is one valid way of gaining a password through local discovery. Do you have a Post-It note on the monitor, or a diary in the desk drawer with your Paypal credentials? There are more covert means of local discovery though, including sniffing bluetooth communicationsor finding plain text passwords in logs or urls. Shoulder-surfing is not unknown, too. That can be anything from a colleague surreptitiously hanging around behind your desk when you login, to CCTV in coffee shops and other public areas that could capture video of users as they type their login credentials into a website on their laptops.How Can You Stay Safe?
There’s no need to be paranoid, but do exercise the proper amount of caution. While the risk is low in general, if you make yourself the low-hanging fruit by leaving easily discoverable records of your password lying around, don’t be surprised if someone takes advantage of that.7. Extortion
Risk Level: Low
Probably lowest on the risk scale, but not unheard of.What Is It?
Somebody demands you give them your credentials. No subtefuge involved. The deal is you give up your password or they do something you won’t like.How Does It Work?
Straightforward blackmail technique that depends on the nature of the relationship between the attacker and the target. Someone may demand your password if they have the means to harm or embarrass you if you don’t comply, such as revealing sensitive information, images or videos about you, or threatening the physical safety of yourself or your loved ones. RAT malware that lets hackers spy on you through a web or video cam can expose you to this kind of extortion.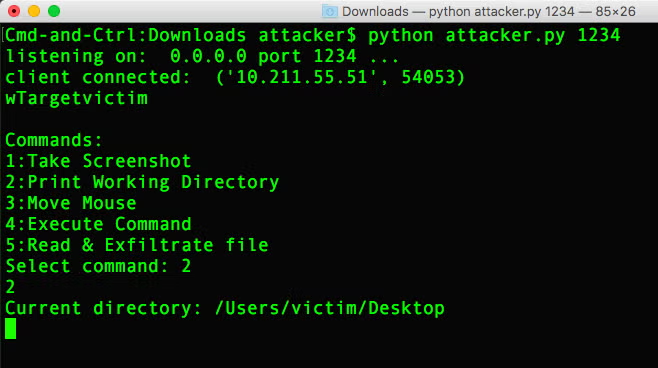
How Can You Stay Safe?
As ransomware victims are finding out on an almost daily basis, there’s no rule book for how to deal with extortion demands. It’s a trade off between the value of what they want versus the value of the harm they could do. Be aware that in some jurisdictions and in certain circumstances, giving in to an extortion demand could make you liable to prosecution under the law.Do Passwords Matter?
Some think not, but yes they do. Strong passwords will protect your from techniques like password spraying and brute force attacks, while unique passwords will protect your from credential stuffing, ensuring that the damage caused by a leak on one site will not negatively impact you elsewhere.Tips For Creating Strong, Unique Passwords
One of the main reasons why Credential Stuffing and Password Spraying are so successful is because people don’t like creating and remembering complex passwords. The good news – which really shouldn’t be news as it’s been true for quite some time – is that password managers will save you the effort. These are readily available and some browsers even have password suggestions built in. Of course, it’s true that these are not foolproof. They typically rely on a master password that, if compromised, exposes all the eggs in your single basket. However, the chances of being a victim of password theft if you use a password manager are significantly lower compared to if you don’t. We suggest the benefits of password managers hugely outweigh the risks, and we highly recommend them as a basic Security 101 practice.
Conclusion
Passwords aren’t going away any time soon, and there’s even good arguments to suggest that they shouldn’t. While biometric data, facial and fingerprint scanning all have a role in helping secure access to services, the one over-riding beauty of a password is it’s the “something you know” and not the “something you have”. The latter can be taken away from you, in some cases legally, but the former cannot, so long as you ensure that it’s sufficiently complex, unique and secret. Combine that with two-factor or multi-factor authentication and your chances of suffering data loss through password hacking are both extremely low and – importantly – highly limited. If an insecure site does leak your credentials, you can be confident that it won’t affect you beyond that particular service.Rich Perry, First Generation Entrepreneur.LifeMost people I know in business have very good Time Management skills. They set out their goals, they prioritise their work and they make a daily task list to get things done. In days gone by that was enough. Forward planning meant that work could be scheduled into the time available. By and large, an organised person could get all their work done quite routinely. Imagine that? The Problem with Time Management But those Time Management techniques were designed for a business world where people had control over their time. It was a business world without Email, mobile phones, i-messenger, apps, i-pads, tablets and social media. Blocks of uninterrupted time were easier to find and in general the plan for the day could be completed as expected. New Challenges Technological advances have completely changed our work environment. Constant communication brings a steady stream of new requests and ever-changing deadlines. Allocating time to a task doesn’t mean it gets done. As soon as we check our email in the morning, our task list is already out of date! And when everything seems urgent it is impossible to stick to our priorities. As the day goes on the work plan can go out the window. Working Reactively The steady stream of requests means comes with an expectation of almost instant response time. So we generally work in a reactive, responsive mode. This great for customer service and team cooperation. But it’s not productive for the achievement of the plans and goals. And ultimately this will impact business growth as the focus becomes less strategic and more operational. Attention Management So in a way Time Management techniques have never been so important. But we need to supplement these techniques with skills to manage our attention. How good are your Attention Management skills? Is this something you have ever thought about? Here are some tips on how you can become more aware of your attention and then how to manage it. Understand Your Attention Do some initial work to understand where your attention is going throughout the day. Spot some patterns, track who and what distracts you. Use a timelog for a few days to get the data on this. Make a list of those attention stealers to remind you what to avoid. Then use a timer so you can check your progress versus your plan during the day. This will help you see where you have drifted on to another task without realising it. But it also helps you get back on track before too much rime has been lost. After a while you develop the skill yourself so the timer isn’t required. Protect Your Attention We often feel obliged to respond to new requests, new E-mails or interruptions. It can be hard to say no to your customers or your colleagues. But we often end up working on something that has a lower priority than the work we planned to do. To give you confidence to make decisions about what you should work on be clear about your responsibilities to your clients or within your role. What is a reasonable response time for clients? What has been agreed? Are you doing tasks that are not in your role? With this knowledge it can be easier to say no or at last negotiate a different response time. Develop the Right Environment If you run your own business take a look at how easy or difficult it is for people to focus. Is there a noise level that can be improved? Can you work together to give each person some “Do Not Disturb” time throughout the week? Encourage people to focus on one task rather than multi-tasking. If your business allows it, turn off the phones at least some of the time. Provide a quiet room as a contrast to the open plan office. Offer your office to your team when you are not there. Allow the use of noise blocking headphones if it doesn’t compromise your service delivery. Above all, be creative. Come up with your own solutions for Attention Management that will suit your business. Be Proactive, Take Control and Be Productive So let’s give some time to Attention Management. It is one of the most important business skills in today’s workplace. Combine this with the classic Time Management techniques and watch your productivity soar.
Janna Herron, USA TODAY
You finally finished your taxes and are learning – for better or worse – the ins and outs of the new law.
But wait, the law isn’t done with you. There’s another complication coming out later this year: The Internal Revenue Service is changing how you adjust your paycheck withholdings, and early indicators show it won’t be easy.
The agency plans to release a new W-4 form that better incorporates the changes ushered in by the new tax law so that the amount held back for taxes in each of your paychecks is more accurate.
The agency’s goal: A taxpayer shouldn’t owe or be owed come tax time.
But the changes won’t be simple, says Pete Isberg, head of government affairs at ADP, the payroll and human resources company.
Filling out the new form will be a lot like doing your taxes again.
“It’ll be a much bigger pain,” he says. “The accuracy will be 100 percent, but the ease-of-use will be zero.”
What’s changing?
While the new form hasn’t been released yet, the IRS last summer put out a draft version and instructions seeking feedback from tax preparation companies and payroll firms. Instead of claiming a certain amount of allowances based on exemptions – which have been eliminated – the draft form asked workers to input the annual dollar amounts for:
- Nonwage income, such as interest and dividends
- Itemized and other deductions
- Income tax credits expected for the tax year
- For employees with multiple jobs, total annual taxable wages for all lower paying jobs in the household
“It looked a lot more like the 1040 than a W-4,” Isberg says.
The new form referenced up to 12 other IRS publications to fill it out. It was so complex and different from the previous W-4 form that Ernst & Young worried employees would struggle to fill it out correctly and employers may need to offer training beforehand.
Why is it taking so long?
The tax and payroll community expressed many concerns about the draft form aside from its complexity.
Many cited privacy issues because the form asked for spousal and family income that workers might not want to share with their employers. Other employees may not want to disclose they have another job or do side work outside their full-time job.
To avoid disclosing so much private information, taxpayers instead could use the IRS withholding calculator, but it’s “not easy to use, and the instructions are confusing,” according to feedback from the American Payroll Association.
In September, the IRS scrapped plans to implement the new W-4 form for 2019 and instead is planning to roll it out for 2020.
What to expect
Another draft version of the new W-4 is expected by May 31, according to the IRS, which will also ask for public comment.
“We encourage taxpayers to take advantage of that opportunity and send us comments on the redesign,” says agency spokeswoman Anny Pachner.
The IRS will review the comments and plans to post a second draft later in the summer. The final W-4 version will be released by the end of the year in time for the 2020 tax year.
Once it arrives, you’ll probably need the following information on hand, says Kathy Pickering, executive director of H&R Block’s Tax Institute. That may mean lugging in past 1099 forms, paystubs or last year’s tax returns to fill it out correctly.
- Your filing status
- Number of dependents
- Information about your itemized deductions such as home mortgage interest, state and local taxes, and charitable deductions
- Earnings from all jobs
- Information about nonwage income such as business income, dividends, and interest.
“If you’re married, and both you and your spouse work, it will also be helpful to know information about your spouse’s income,” she says.
You may also need to fill out a new state income withholding form. Many states use the current W-4 for withholding, but they may need to release their own forms, too.









